An ongoing cyber assault marketing campaign has set its sights on Korean-speaking people by using U.S. Navy-themed doc lures to trick them into working malware on compromised techniques.
Cybersecurity agency Securonix is monitoring the exercise below the title STARK#MULE.
“Based mostly on the supply and certain targets, these kind of assaults are on par with previous assaults stemming from typical North Korean teams equivalent to APT37 as South Korea has traditionally been a main goal of the group, particularly its authorities officers,” safety researchers Den Iuzvyk, Tim Peck, and Oleg Kolesnikov stated in a report shared with The Hacker Information.
APT37, additionally identified by the names Nickel Foxcroft, Reaper, Ricochet Chollima, and ScarCruft, is a North Korean nation-state actor that is identified to completely concentrate on targets in its southern counterpart, particularly these concerned in reporting on North Korea and supporting defectors.
Assault chains mounted by the group have traditionally relied on social engineering to phish victims and ship payloads equivalent to RokRat onto goal networks. That stated, the adversarial collective has expanded its offensive arsenal with a wide range of malware households in latest months, together with a Go-based backdoor known as AblyGo.
A notable trait of the brand new marketing campaign is the usage of compromised Korean e-commerce web sites for staging payloads and command-and-control (C2) in an try and fly below the radar of safety options put in on the techniques.
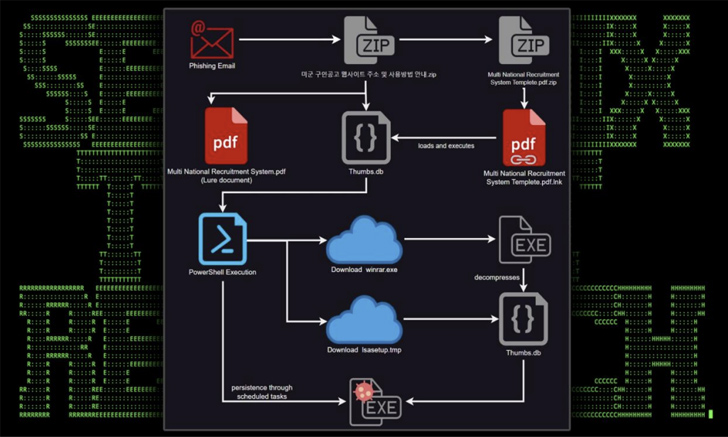
The phishing emails that act because the progenitor make use of U.S. Military recruitment messages to persuade recipients into opening a ZIP archive file, which incorporates a shortcut file that seems below the guise of a PDF doc.
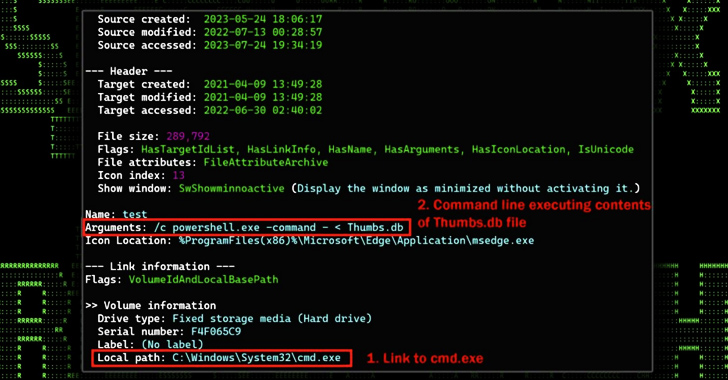
The shortcut file, when launched, shows a decoy PDF, but in addition surreptitiously prompts the execution of a rogue “Thumbs.db” file current within the archive file.
“This file performs a number of capabilities which embrace downloading additional stagers and leveraging schtasks.exe to ascertain persistence,” the researchers defined.
Two of the next-stage modules – “lsasetup.tmp” and “winrar.exe” – are retrieved from a compromised e-commerce web site named “www.jkmusic.co[.]kr,” the latter of which is used to extract and run the contents of “lsasetup.tmp,” an obfuscated binary that reached out to a second e-commerce website named “www.notebooksell[.]kr.”
“As soon as the connection was established, the attackers had been in a position to purchase system particulars equivalent to system MAC, Home windows model, [and] IP handle,” the researchers stated. “Each web sites are registered in Korea [and] solely make the most of the HTTP protocol.”
The disclosure comes as APT37 has additionally been noticed making use of CHM recordsdata in phishing emails impersonating safety emails from monetary institutes and insurance coverage firms to deploy information-stealing malware and different binaries, in accordance with the AhnLab Safety Emergency Response Heart (ASEC).
“Specifically, malware that targets particular customers in Korea might embrace content material on matters of curiosity to the consumer to encourage them to execute the malware, so customers ought to chorus from opening emails from unknown sources and shouldn’t execute their attachments,” ASEC stated.
Defend In opposition to Insider Threats: Grasp SaaS Safety Posture Administration
Anxious about insider threats? We have you lined! Be a part of this webinar to discover sensible methods and the secrets and techniques of proactive safety with SaaS Safety Posture Administration.
APT37 is among the many North Korean state-sponsored teams which have drawn consideration for executing assaults which are designed to perpetrate monetary theft – together with the latest assaults on Alphapo and CoinsPaid – and collect intelligence in pursuit of the regime’s political and nationwide safety goals.
This additionally includes the infamous Lazarus Group and its sub-clusters Andariel and BlueNoroff, with the actors leveraging a brand new backdoor dubbed ScoutEngine and a totally rewritten model of a malware framework known as MATA (MATAv5) in intrusions aimed toward protection contractors in Jap Europe in September 2022.
“This refined malware, fully rewritten from scratch, displays a complicated and complicated structure that makes use of loadable and embedded modules and plugins,” Kaspersky stated in its APT developments report for Q2 2023.
“The malware leverages Inter-Course of Communication (IPC) channels internally and employs a various vary of instructions, enabling it to ascertain proxy chains throughout numerous protocols, together with throughout the sufferer’s atmosphere.”